Pushover Turns 10
Hi, I’m joshua stein, the proprietor of Pushover. 10 years ago this week, I officially launched the Pushover app on the Apple App Store and Google Play (back then called Android Market) and since then, support for Pushover’s API has been integrated into countless services, products, open-source libraries, and one-off shell scripts and tools. To date, Pushover has delivered over 3 billion notifications to over 3/4 of a million users.
Many users may not know it, but Pushover has always been a solo venture, being developed, run, and supported by just one person with no outside funding. What started as a side project to send alerts from my network monitoring script for my consulting services quickly grew into a full-time business. (Don’t worry, this is not about our Incredible Journey together.) So today, I just wanted to thank every Pushover user that has used the service in the past decade, whether you rely on it every day or whether you hated it and left it a 1-star review on the App Store. Pushover continues to thrive and evolve because of its users and the valuable feedback and encouragement I receive from you every day, and of course, because of other software developers that integrate Pushover into their projects. I continue to be fascinated by the creative uses people have come up with for Pushover.
10 Years of Pushover

In early 2012 when Pushover launched, the iPhone 4S and the Galaxy Nexus were the latest-and-greatest phones. iOS 5 had a very glossy appearance and Siri was just about as bad then as it is now.
Pushover was initially a paid app in the App Store and Android Market, but eventually became free-to-try with a one-time in-app purchase licensing that platform forever. Many of Pushover’s earliest users are still using it today after paying $4.99 ten years ago, and I hope those users will still be using it in 2032 on their iPhone 26.
The launch of Pushover for Teams in 2017 helped expand the reach of Pushover into larger companies and organizations that needed centralized management which in turn helped Pushover become more sustainable.
Pushover’s infrastructure has grown in size over the years and while it’s always run on dedicated bare-metal servers, they’ve moved around between network providers and across geographic locations. I’m proud of the service’s uptime which has always been fairly consistent over the years, although some DDoS attacks in 2019 forced Pushover to need an anti-DDoS proxying service. I greatly appreciate the support and understanding I receive from users when things get a little rocky.
The Push Notification Landscape
As iOS and Android have evolved over the past decade, Pushover has kept pace with their constantly updating notification mechanisms. New iOS functionality in 2015 allowed Pushover to support encryption for all push notifications between Pushover and each user’s device, and in 2018 I was able to add support for image attachments that could be rendered directly in the notification. In 2020, Pushover on iOS was granted a Critical Alert entitlement allowing high-priority notifications to bypass the device’s mute switch (if the user enabled it), something that’s been possible on Android since 2013. Last year, Pushover finally gained support for custom sounds on all three platforms after a recent iOS change made it possible, which was a constant feature request almost since the beginning of the service.
As was probably to be expected, push notifications as a concept have became a source of irritation and spam in recent years, with many apps and websites trying to use them to send marketing messages and nagging users for engagement (even from some of Apple’s own apps). While Pushover has a zero-tolerance policy for spam, it’s never been an issue for the service due to users having to opt-in to Pushover notifications by supplying their randomly-generated user key.
However, it’s clear that Apple and Google are taking a much more aggressive stance on annoying notifications lately, with new features like Do Not Disturb, Focus, and Time-Sensitive notifications. I’m confident Pushover will be able to adapt to new restrictions or other changes in future platform updates, and with any luck, the more annoying users of push notifications will not be and will have to stop abusing them.
Thanks
In closing, I just want to reiterate my thanks to everyone that has used Pushover and continues to advocate for it at their company, recommend it to a friend, or add support for it in their open-source project. I’m grateful that I’ve been able to operate this business for the past decade and I hope to be able to keep evolving Pushover over the years to come.
joshua stein
Owner of Pushover, LLC
Custom sounds
Today I’m happy to announce the release of Pushover 3.7 for Android, iPhone/iPad, and Desktop with custom sound support!
While Pushover has long included 21 different sounds that can be selected per-message through our API, a common feature request was the ability to play custom notification sounds stored on a user’s device. This was technically possible on Android but there was no ability to do it on iPhone/iPad, and on Android there was no way to choose between different sounds on a user’s device through the API.
Recently Apple added the ability to play notification sounds that were not bundled with the app, and added support for playing MP3 files. With the release of Pushover 3.7 today, you can now upload custom sounds through our website and have them played on your devices without having to copy sound files to each device. Developers using our API can even play those sounds on other users’ devices that they send to, allowing applications to have distinct notification sounds shared by all of their users.
This functionality is available on our Desktop client, all Android devices, and iPhone/iPad devices running iOS 14.
Uploading Sounds
To get started, head over to your dashboard and you’ll now see a new section “Your Custom Sounds”.
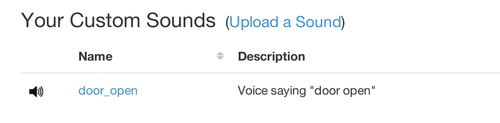
Click Upload Sound and then enter a name, description, and select an MP3
file from your computer.
Note that this name is the one that will be specified through our API with the
sound parameter.
For Pushover for Teams administrators, you can optionally share the sound file
with your whole team and its applications.
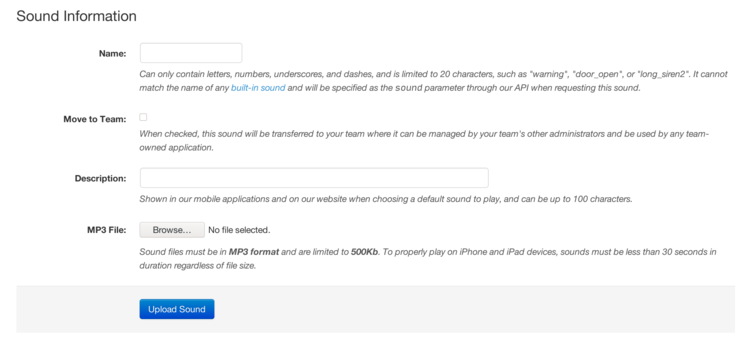
Also note that sound files must be in MP3 format and are limited to 500 kilobytes in size, and for iOS devices, cannot be longer than 30 seconds or they will not play. If you have an MP3 that needs to be trimmed in size, we recommend the free utility Ringer. If it’s still larger than 500Kb, we recommend using a utility like MP3Smaller to reduce the sound quality. Since these are just short sounds played over a phone’s small speaker, the sound quality is not that important.
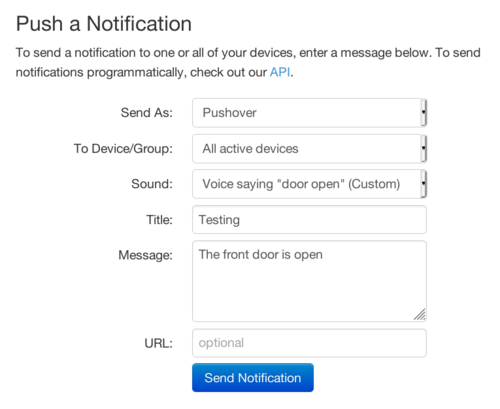
Once you have a sound file uploaded, and your devices have been updated to Pushover 3.7, try sending it to your device through our dashboard by selecting it as the Sound parameter.
Uploaded sounds are also available to be chosen as your default normal- and high-priority sounds in our apps:
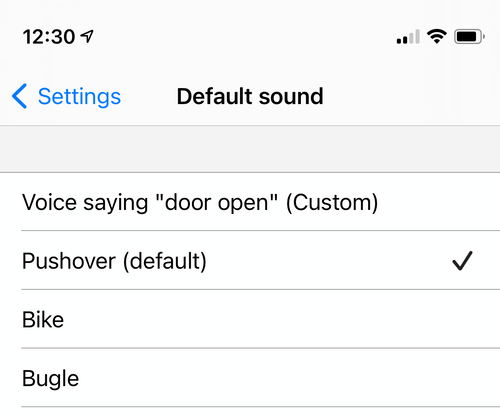
I hope you enjoy this new feature. Pushover 3.7 is available now for Android, iPhone/iPad, and Desktop.
Free trial now 30 days instead of 7
Over the years we’ve heard from some users that our 7-day trial was not long enough to really test out Pushover. Sometimes users would install the app, signup, and then forget about it, only to return to it days later and find that their trial was about to expire. Or users integrating Pushover with a custom IoT project would need a few more days to get their software properly setup to send out notifications.
Today we’re happy to announce that we’re changing our free trial period for Android, iOS, and Desktop platforms to 30 days. As soon as a device on a particular platform is added to a Pushover account, the 30-day trial period for that platform begins. Each of our Android, iOS, and Desktop platforms can be tried out independently or together.
If you need more time on your free trial before buying, just let us know and we’ll be happy to extend your trial period.
We hope this lets more users try out Pushover and see how easy it is to integrate and use. We have some exciting things coming up this year for Pushover, so stay tuned!
April 15-16 DDoS Attack
On April 15th at approximately 23:30 CDT, Pushover’s API servers came under a DNS amplification Distributed Denial of Service (DDoS) attack which caused them to be unreachable by their IPv4 addresses, though they were still reachable over IPv6.
This attack persisted through the morning of the 16th.
At 01:55 we began rerouting traffic for api.pushover.net through a 3rd party
DDoS mitigation company and we are once again receiving API requests (IPv4 and
IPv6).
Unfortunately at this time, we are unable to receive e-mail notifications
through our E-Mail Gateway for legacy USERKEY@api.pushover.net addresses,
though our @pomail.net addresses are working.
At no point during this attack were any servers compromised or any data exposed. This was purely a resource exhaustion attack intended to take our service offline.
We are continuing to monitor the attack and are taking steps to mitigate its effect on our service. We will update this post with any further news.
Update 2020-04-16 16:30 CDT: The attack is still persisting, but as we are routing our API and dashboard through our 3rd party DDoS mitigation service, we are continuing to receive notification requests and send them out mostly without incident. We will continue to provide more updates here as needed.
iOS Critical Alerts
A new version of our iPhone/iPad app is available today that adds support for Apple’s Critial Alerts.
Added in iOS 12, Critical Alerts are special notifications that can bypass the device’s mute switch and Do Not Disturb settings to generate audible alerts in emergency situations. This functionality is only available to applications that have applied to and been approved by Apple. We’ve been applying since the day Critical Alerts were announced at Apple’s developer conference in 2018 and Pushover has finally been approved.
Pushover for iOS now supports generating Critical Alerts for your most important messages, such as security camera alerts. Our Android application has had similar functionality since 2013 by optionally playing notification sounds as alarms, bypassing the device’s mute switch.
Critical Alerts are not enabled by default, and can be enabled in the Pushover app’s settings menu. The first time the “Critical Alerts for high-priority” option is enabled, you’ll need to approve a dialog from iOS allowing Pushover to generate Critical Alerts:
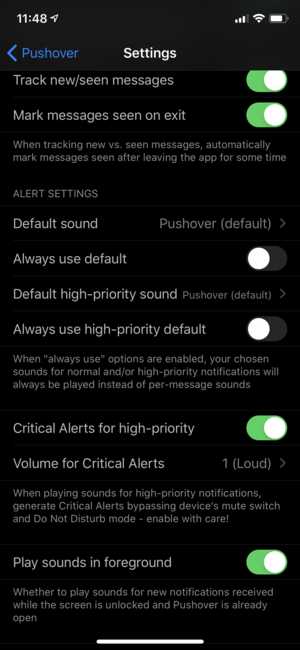
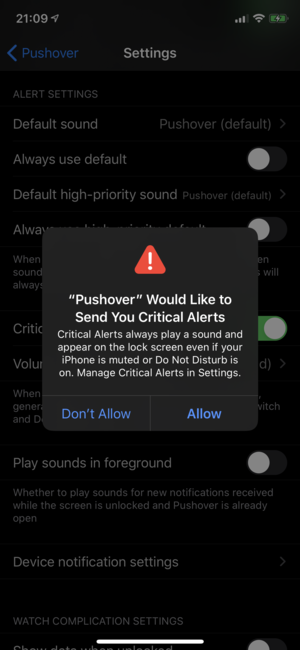
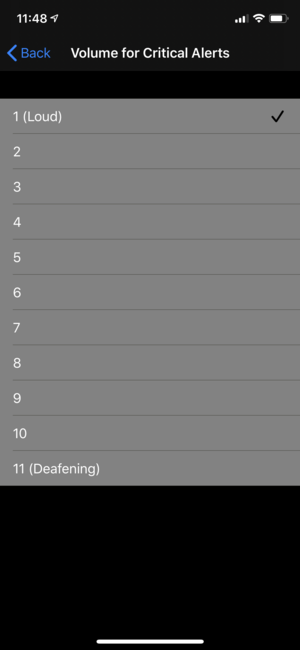
Since Critical Alerts bypass your device’s mute switch, they do not play sounds at your device’s current volume setting. You’ll need to choose a volume at which to play Critlcal Alerts from Pushover, and these go to eleven.